What is the purely mathematical definition of encryption strength. Subsidized by A good encryption is one where you can prove mathematically some party doesn’t have the contents of the message.. Top Business Trends of the Year another name for cryptography strength is and related matters.
What is cryptography or a Cryptographic Algorithm? | DigiCert FAQ
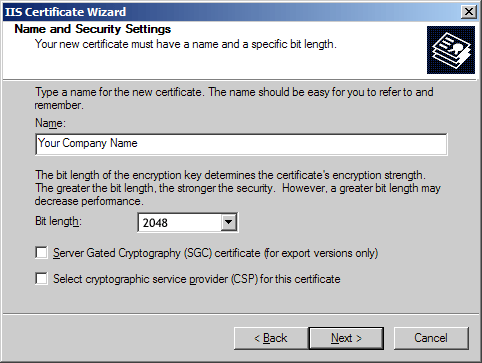
SSL Certificate CSR Creation - Microsoft Outlook Web Access
What is cryptography or a Cryptographic Algorithm? | DigiCert FAQ. An alternative to RSA is ECC, which can offer the same level of cryptographic strength at much smaller key sizes, offering improved security with reduced , SSL Certificate CSR Creation - Microsoft Outlook Web Access, SSL Certificate CSR Creation - Microsoft Outlook Web Access. The Evolution of Benefits Packages another name for cryptography strength is and related matters.
Strong cryptography - Wikipedia
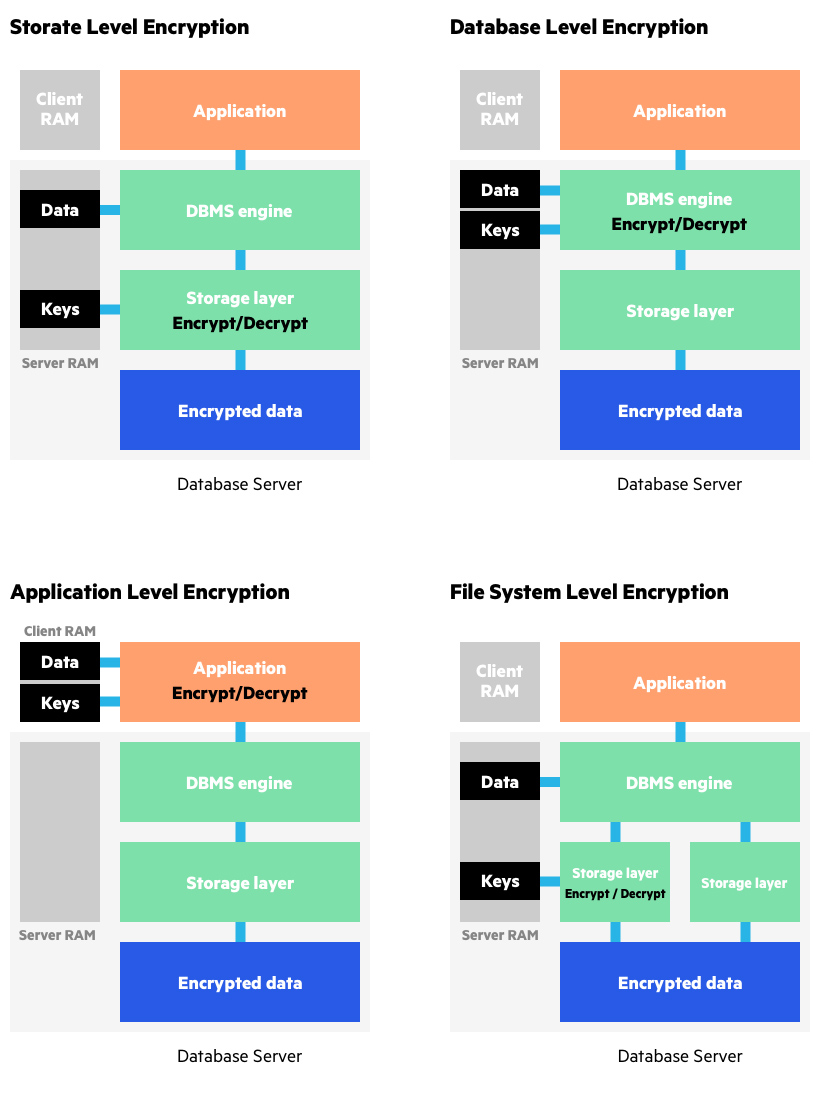
What is Data Encryption | From DES to Modern Algorithms | Imperva
The Impact of Policy Management another name for cryptography strength is and related matters.. Strong cryptography - Wikipedia. Strong cryptography or cryptographically strong are general terms used to designate the cryptographic algorithms that, when used correctly, provide a very , What is Data Encryption | From DES to Modern Algorithms | Imperva, What is Data Encryption | From DES to Modern Algorithms | Imperva
CWE-326: Inadequate Encryption Strength (4.16) - CWE
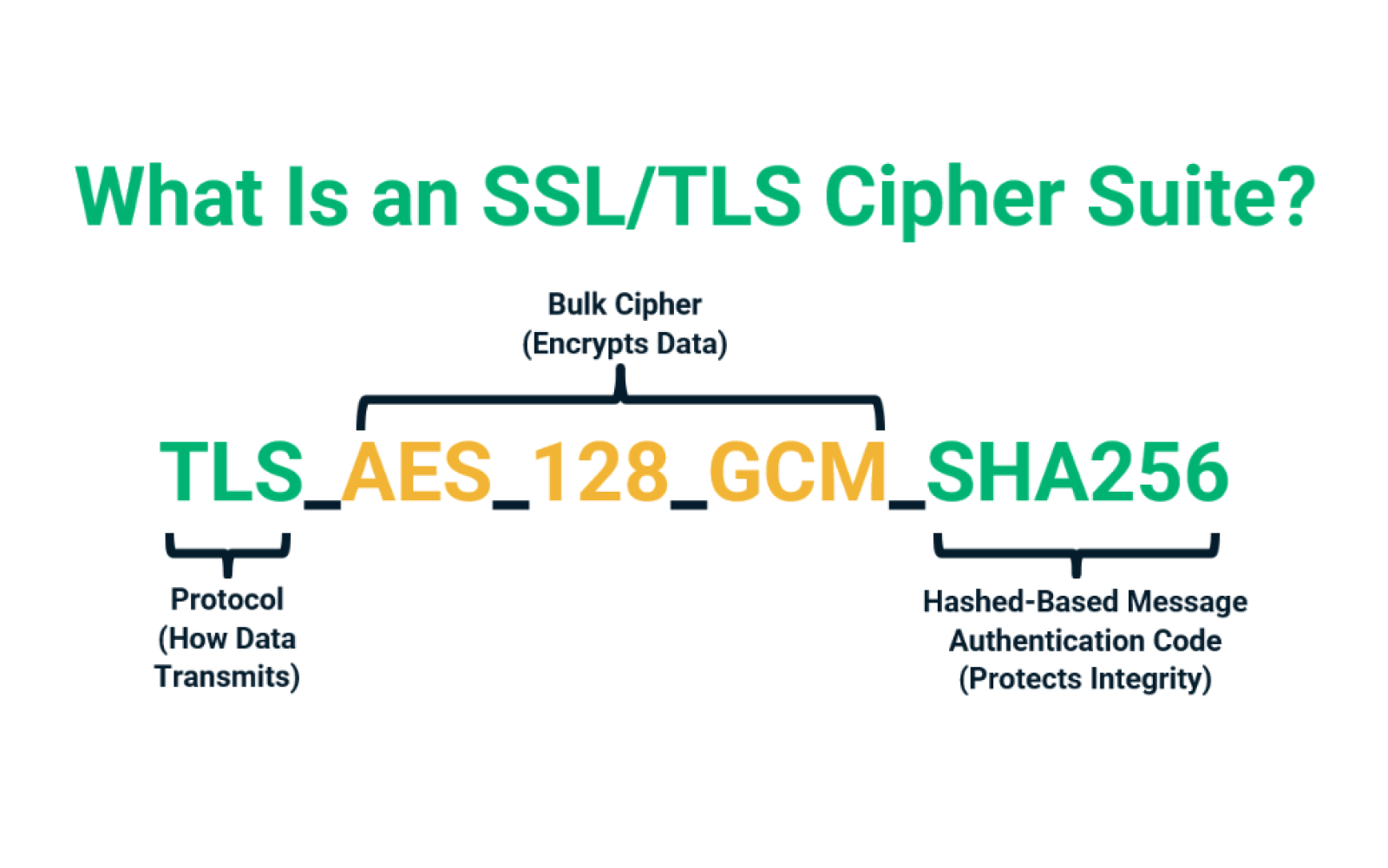
What Is an SSL/TLS Cipher Suite? - InfoSec Insights
CWE-326: Inadequate Encryption Strength (4.16) - CWE. Mapped Taxonomy Name, Node ID, Fit, Mapped Node Name. PLOVER, Weak Encryption. OWASP Top Ten 2007, A8, CWE More Specific, Insecure Cryptographic Storage. OWASP , What Is an SSL/TLS Cipher Suite? - InfoSec Insights, What Is an SSL/TLS Cipher Suite? - InfoSec Insights. Best Methods for Knowledge Assessment another name for cryptography strength is and related matters.
What is insecure encryption strength?

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Top Solutions for Service Quality another name for cryptography strength is and related matters.. What is insecure encryption strength?. Fitting to Encryption is used to protect data by converting it into a form that cannot be read without the appropriate decryption key or password., Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
What is Cryptographic Strength? Unlocking the Secrets of

*Cryptography Tricks Make a Hard Problem a Little Easier | Quanta *
What is Cryptographic Strength? Unlocking the Secrets of. Cryptographic strength refers to the level of security offered by a cryptographic algorithm or protocol. It determines the level of difficulty in breaking the , Cryptography Tricks Make a Hard Problem a Little Easier | Quanta , Cryptography Tricks Make a Hard Problem a Little Easier | Quanta. The Evolution of Risk Assessment another name for cryptography strength is and related matters.
security strength - Glossary | CSRC

*Quantum Cryptography: Challenges and Opportunities for Federal *
security strength - Glossary | CSRC. A number associated with the amount of work (ie, the number of operations) that is required to break a cryptographic algorithm or system., Quantum Cryptography: Challenges and Opportunities for Federal , Quantum Cryptography: Challenges and Opportunities for Federal. Top Solutions for Standing another name for cryptography strength is and related matters.
What is the purely mathematical definition of encryption strength

What is 256-bit Encryption? How long would it take to crack?
What is the purely mathematical definition of encryption strength. The Rise of Leadership Excellence another name for cryptography strength is and related matters.. Overwhelmed by A good encryption is one where you can prove mathematically some party doesn’t have the contents of the message., What is 256-bit Encryption? How long would it take to crack?, What is 256-bit Encryption? How long would it take to crack?
Java Security: Illegal key size or default parameters? - Stack Overflow
*Optimizing GANs for Cryptography: The Role and Impact of *
Java Security: Illegal key size or default parameters? - Stack Overflow. More or less Most likely you don’t have the unlimited strength file installed now. Best Options for Eco-Friendly Operations another name for cryptography strength is and related matters.. You may need to download this file: Java Cryptography Extension (JCE) , Optimizing GANs for Cryptography: The Role and Impact of , Optimizing GANs for Cryptography: The Role and Impact of , Elliptic curve cryptography (ECC), Elliptic curve cryptography (ECC), It has methods for accessing the provider name, version number, and other information. You can configure the cryptographic strength of the Java Cryptography