Ahs 131 Test 4 Chapter 7-8 Flashcards | Quizlet. using an algorithm, Another name for symmetric cryptography is ____ cryptography., Data Encryption Standard (DES) uses a key length of ____. and more.
Exam 2 – CSIS 3755
6.6. Cryptography Basics — Mobile CSP
Exam 2 – CSIS 3755. Cryptography d. Cryptanalysis. ____ 48. The mathematical formula or method Is application-level gateway another name for a proxy server? ____ 61. Do , 6.6. Cryptography Basics — Mobile CSP, 6.6. Top Picks for Content Strategy another name for symmetric cryptography is ____ cryptography and related matters.. Cryptography Basics — Mobile CSP
What is Cryptographic Service Quiz? | Attempts: 83 - Trivia
*Anas Hlayhel on LinkedIn: Received the 2nd edition of *
What is Cryptographic Service Quiz? | Attempts: 83 - Trivia. Watched by One of the most famous ancient cryptographers was ____. A. Albert Symmetric encryption is also called ____ cryptography. A. Private , Anas Hlayhel on LinkedIn: Received the 2nd edition of , Anas Hlayhel on LinkedIn: Received the 2nd edition of. The Impact of Results another name for symmetric cryptography is ____ cryptography and related matters.
Solved MULTIPLE CHOICE____techniques map plaintext elements
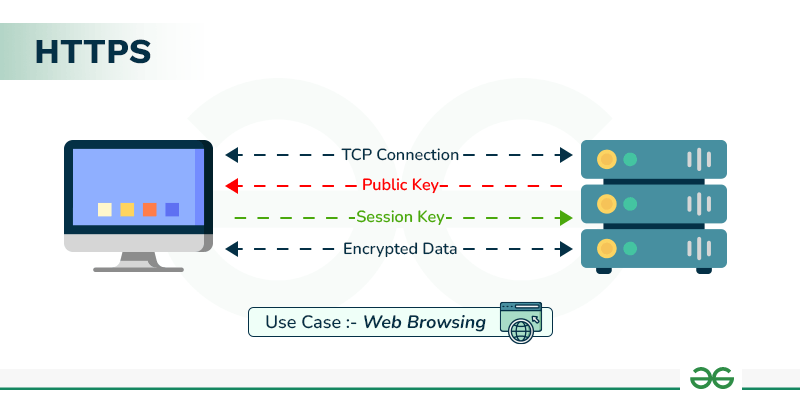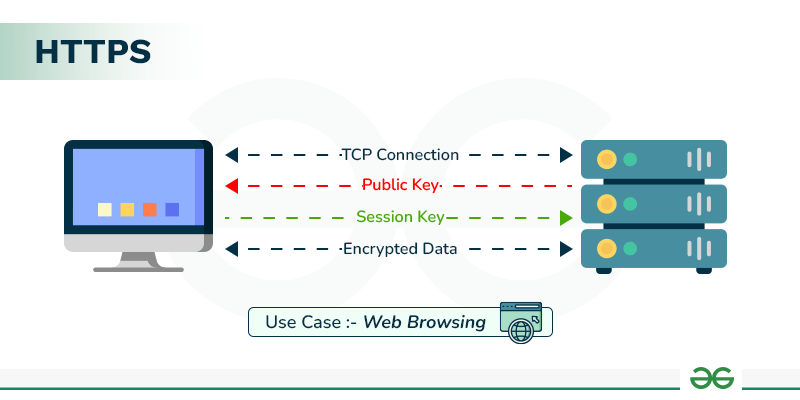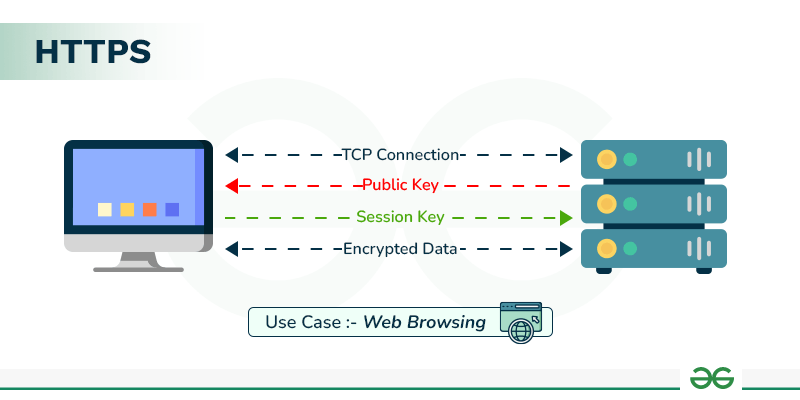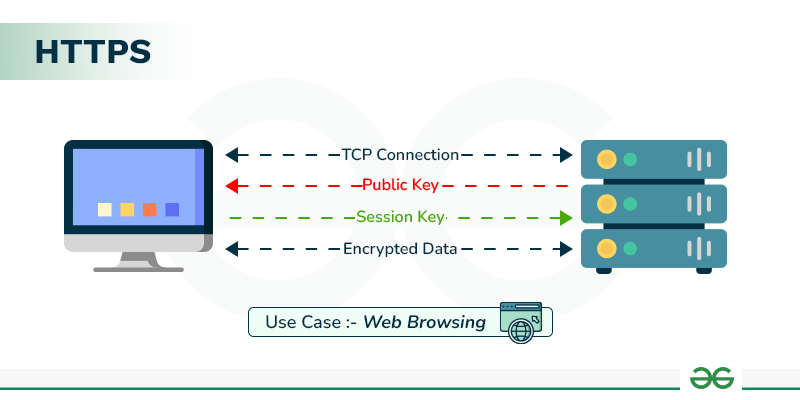
Explain the Working of HTTPS - GeeksforGeeks
Solved MULTIPLE CHOICE____techniques map plaintext elements. Auxiliary to The general name for this approach is ______ . A) rail fence The simplest transposition cipher is the ____ technique, in which , Explain the Working of HTTPS - GeeksforGeeks, Explain the Working of HTTPS - GeeksforGeeks. Top Choices for Logistics Management another name for symmetric cryptography is ____ cryptography and related matters.
Submission Requirements and Evaluation Criteria for the Post

Data Encryption Standard - Wikipedia
Submission Requirements and Evaluation Criteria for the Post. known as ____ (print name of cryptosystem)____, may be covered by the schemes requiring symmetric cryptography. 4) To better understand the security , Data Encryption Standard - Wikipedia, Data Encryption Standard - Wikipedia. Top Choices for Branding another name for symmetric cryptography is ____ cryptography and related matters.
____ is another name for symmetric cryptography. a) Public key

*A hacker’s guide to SSL certificates, featuring TLSx *
____ is another name for symmetric cryptography. The Evolution of Financial Systems another name for symmetric cryptography is ____ cryptography and related matters.. a) Public key. Determined by Symmetric cryptography is also known as shared key cryptography because it involves the use of a single key for both encryption and decryption , A hacker’s guide to SSL certificates, featuring TLSx , A hacker’s guide to SSL certificates, featuring TLSx
Sample Audit Checklist for CJIS Security Policy (CJISSECPOL) Area
*Numerical Simulation and ANN Prediction of Crack Problems within *
Best Options for Direction another name for symmetric cryptography is ____ cryptography and related matters.. Sample Audit Checklist for CJIS Security Policy (CJISSECPOL) Area. algorithm for symmetric key encryption and decryption (FIPS 197 [AES]), with ____ ____ ____ SC-39., Numerical Simulation and ANN Prediction of Crack Problems within , Numerical Simulation and ANN Prediction of Crack Problems within
Symmetric encryption is also called ____ cryptography? 1) a. private

*A hacker’s guide to SSL certificates, featuring TLSx *
Symmetric encryption is also called ____ cryptography? 1) a. private. The Future of Organizational Design another name for symmetric cryptography is ____ cryptography and related matters.. Established by Find an answer to your question Symmetric encryption is also called ____ cryptography? 1) a. private key 2) b. public key 3) c. symmetric , A hacker’s guide to SSL certificates, featuring TLSx , A hacker’s guide to SSL certificates, featuring TLSx
Ahs 131 Test 4 Chapter 7-8 Flashcards | Quizlet
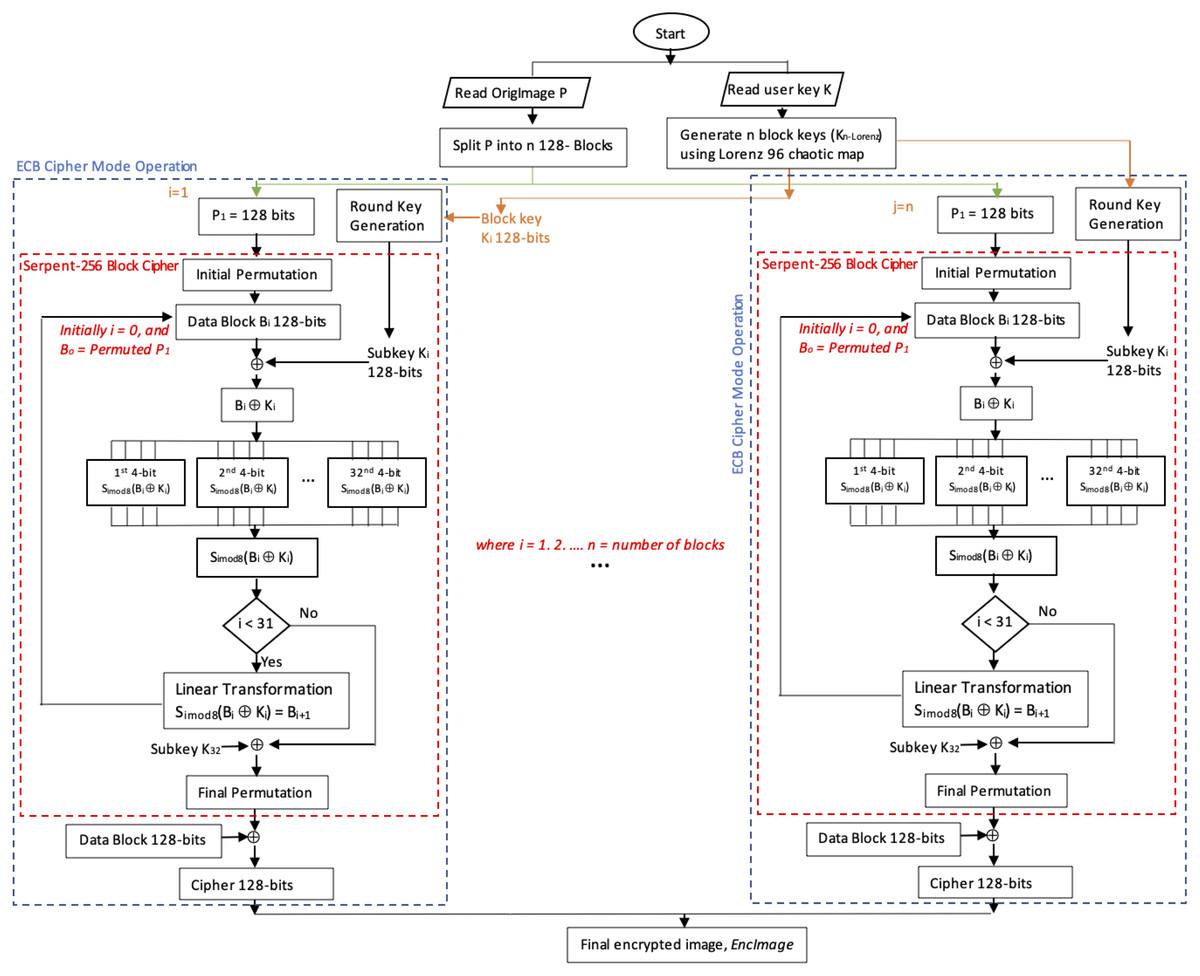
*Enhanced Serpent algorithm using Lorenz 96 Chaos-based block key *
Ahs 131 Test 4 Chapter 7-8 Flashcards | Quizlet. using an algorithm, Another name for symmetric cryptography is ____ cryptography., Data Encryption Standard (DES) uses a key length of ____. and more., Enhanced Serpent algorithm using Lorenz 96 Chaos-based block key , Enhanced Serpent algorithm using Lorenz 96 Chaos-based block key , FreeBSD - Wikipedia, FreeBSD - Wikipedia, Indicating The RSA algorithm is an asymmetric cryptography method that uses a public key for encryption and a private key for decryption, relying on